Zap
8 Key Concepts and Features of the ZAP Scanner
1. Active Scan
Active scanning uses known attacks to identify potential vulnerabilities, which means it can only find specific vulnerabilities. Active or automatic vulnerability scans cannot find errors in application logic. It is possible only while conducting a manual audit.
2. Passive Scan
By default, ZAP scans HTTP requests and all responses sent and received from your application. Passive scanning does not affect their content. You can add tags or alerts to inform you about any potential errors. While this option is enabled by default, it is also possible to configure it.
3. OWASP ZAP Fuzzer
OWASP ZAP lets you use a fuzzer that sends many unexpected or incorrect data to a tested application. You can create your own payloads, use any of the built-in payloads, or download the payloads add-ons provided by the ZAP community.
4. OWASP ZAP API
OWASP ZAP provides an API that accepts JSON, XML, and HTML. The API’s functionality is explained on a web page, specifying that the default allows only the machine running ZAP to connect to the API. However, you can use the configuration options to allow other machines to contact the API.
5. WebSocket Testing
WebSockets are highly pervasive across applications. ZAP lets you easily intercept, analyze, or tamper with the WebSocket traffic between client and server. You can access the WebSocket Message editor by going to the ZAP Menu, choosing Tools, and then selecting WebSocket Message Editor. Use the editor to tamper with the Direction, Opcodes, or the WebSocket message before it is sent back to the server.
6. JAX Spidering
You perform AJAX spidering during a penetration test to identify requests on an AJAX-rich web application. You cannot identify these requests with a standard spidering tool. You can access the AJAX spidering window by going to the menu bar, choosing Tools, and then selecting AJAX Spider (on). This tool includes configuration parameters like maximum depth to crawl, maximum duration, maximum crawl states, and other options to help you prevent infinite crawling.
7. Scan Policy Management
ZAP lets you compose a scan policy according to specific requirements for each application. You can find the Scan Policy Manager under the menu bat. Go to Analyze, and then choose Scan Policy Manager.
Penetration testers need to optimize this scanner according to the target application’s abilities to keep up with the app’s operational performance and prevent DoS. While creating scan policies, you must consider the scanner machine’s bandwidth and processing capabilities.
You can alter a scan policy to exclude or include the test to perform. ZAP also lets you configure the definition of parameters such as:
Threshold—the likelihood of flagging a potential vulnerability
Strength—the number of requests for each of the tests
Penetration testers usually need to test the scenarios they might frequently encounter across the target application. ZAP lets you design a custom scan policy that you can export as a template. You can import the scan policy back into ZAP and reuse it.
8. ZAP Marketplace
ZAP Marketplace includes free and open source add-ons written by the ZAP team as well as the community. These add-ons enable you to extend the functionality of a ZAP implementation. You can browse the marketplace and download add-ons by going to the toolbar, clicking on the Manage Add-ons button, and then choosing the Marketplace tab.
Related content: Read our guide to owasp mobile top 10.
OWASP ZAP Tutorial: Install and Configure OWASP ZAP
ZAP provides installers for Linux, Mac OS/X, and Windows. The download page also provides Docker images.
Choose the appropriate installer
Go to the download page and install ZAP for the system you intend to perform penetration testing on.
Here are the requirements for ZAP and each installer:
ZAP requires Java 8+ to run.
The Mac OS/X installer comes with Java 8+.
Linux, Windows, and the various cross-platform versions require installing Java 8+ separately.
Docker versions do not require installing Java at all.
Determine whether to persist the session
Once you start installing ZAP, you need to specify if you want to persist this ZAP session. ZAP sessions are recorded by default to the disk in an HSQLDB database that gets a default location and name. If you choose not to persist a session, the files are deleted once you exit ZAP.
If you decide to persist this session, all session information is saved within the local database. ZAP lets you provide custom locations and names for saving the files. You can access the database later.
Key components of the desktop user interface (UI)
ZAP’s desktop UI is composed of the following elements:
Menu Bar—lets you access ZAP’s manual and automated tools.
Toolbar—provides easy access to commonly used ZAP features.
Tree Window—displays the Scripts tree and Sites tree.
Workspace Window—displays responses, scripts, and requests and lets you edit them.
Information Window—displays the details of manual and automated tools.
Footer – displays a summary of all alerts and the status of all main automated tools.
Image Source: OWASP
Using the Quick Start tab
The Quick Start tab is an add-on included with your ZAP installation, which can help you get started with ZAP. Here is how you can run a Quick Start Automated Scan:
Start ZAP, go to the Workspace Window, select the Quick Start tab, and choose the big Automated Scan button.
Go to the URL to attack text box, enter the full URL of the web application you intend to attack, and then click the Attack button.
Image Source: OWASP
How ZAP attacks work
Once you click the Attack button, ZAP starts crawling the web application with its spider, passively scanning each page it finds. Next, ZAP uses the active scanner to attack all discovered pages, parameters, and functionality.
ZAP includes two spiders that can crawl web applications. You can use one or both of the spiders. Here are key differences between the spiders:
A traditional ZAP spider—this spider discovers links by examining the HTML in responses from a web app. It is fast but not always effective when you want to explore AJAX web applications that generate links using JavaScript.
ZAP’s AJAX spider—this spider is for AJAX applications. It explores a web application by invoking browsers, which then follow all the links that were generated. It is slower than the traditional spider and requires extra configuration when using it in a “headless” environment.
Passive vs. active scanning
ZAP passively scans all responses and requests that are proxied through it. This type of scanning does not change responses, which is why it is generally considered safe. The scanning is performed in a background thread so as not to slow down exploration.
Summary
This is the last article in the ZAP series. In this piece, I will explain some of the main features of ZAP: Sessions, Generating Vulnerability Assessment Reports, Passive Scanning, Active Scanning, Scan Policy Manager
Description
This is the last article in the ZAP series. In this piece, I will explain some of the main features of ZAP I didn't cover in the previous part. Before we even start, I will remind you that this tool should be used just on the applications created for testing or the applications you would need to test.
We will divide this part of the series to cover a few topics:
Sessions
Generating Vulnerability Assessment Reports
Passive Scanning
Active Scanning
Scan Policy Manager
Sessions
In the second part of the ZAP series, I mentioned sessions when we ran ZAP for the first time. I will summarize that.
When you run the ZAP tool, this window will pop up:
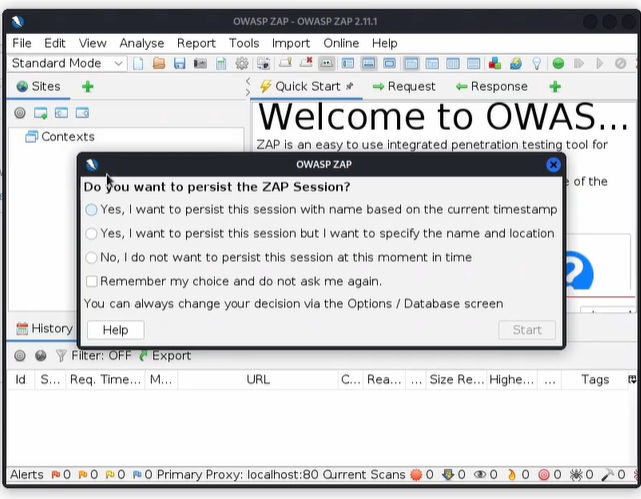
I will also paste some explanation from the mentioned article about the third option when you don't want to save the session:
We can select no, and if we want to save the session, we can do it at a later time.
If you choose to save the session, it will be saved to the disk in an HSQLDB database. The database gets a default location and name. You can access the db later. If you don't persist a session, the files are deleted once you exit ZAP.
If we choose the first option: Yes, I want to persist this session with name based on the current timestamp the session will be stored in db folder directly and name will be based on the current timestamp. Mainly the mentioned folder where sessions will be stored is located in "%HOMEPATH%\OWASP ZAP\sessions" if you are using Windows or Kali, it is usually like in the picture below.

If we close the saved ZAP session and we want to open some other saved session, we should click on File > Open Session and find the session in its appropriate path.
If we choose the second option: Yes, I want to persist this session, but I want to specify the name and location new window will appear where you can type the desired fields. There is also a way to create a new session by clicking on the File tab > Persist Session. You can choose the location and the session's name in the pop-up window.
There is also an option to compare two sessions. We can compare the current(opened) session with some previously saved ones by clicking on the Report tab > Compare with another session.
The other option ZAP provides is modifying the saved (current) session. That can be achieved by clicking on File > Snapshot Session As. Please don't let the name "snapshot" fool you; imagine this option as Save As.
In pentesting, it is very important to organize your tests, so creating sessions will help you with better organization.
Next thing which is important for pentesters is making vulnerability assessment reports.
Generating Vulnerability Assessment Reports
This feature is not just important to provide for the management or the stakeholders. It is also important to collect history records of testing during the time so you can compare reports and make a conclusion about it.
When security testing is finished and you collect all results, you can start generating the report.
It is very important that we leave the sites we want to include in the report in the side tree (we can select all unnecessary sites and delete them). Then we will click on the Report tab > Generate Report, and the next window appears.
There are a few sections/tabs you can see. In the scope tab, you fill out basic information regarding the report file, but in other tabs: Template and Filter, you can specify what report will include.

The report will be saved as HTML and opened in the browser. It will be divided into sections you choose in the Template section.
There will be section Summaries, and you will be able to see, for example alert counts by alert type:

Passive Scanning
ZAP automatically performs Passive Scanning in the background thread by scanning all HTTP requests and responses. It doesn't change the requests or the responses in any way.
Passive Scan Report Rules define what kind of vulnerabilities to check in the background.
To check out the Passive Scan Rules list, go to Tools > Options > Passive Scan Rules
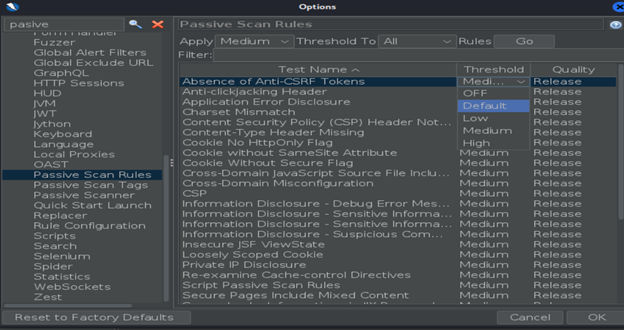
Check out the list! Here you can also manage how ZAP will perform the scan – you can choose the threshold of all vulnerabilities. A Passive Scanner is also an option where you can set up the

All options can be seen in the picture, and you can manage if the scan will be performed just for some specific scope, the maximum number of alerts, etc. For more information about passive scan options, you can check out this site.
There is also a useful option called Passive Scan Tags. To read more about it you can visit this site.
Active Scanning
Active scanning attempts to find potential vulnerabilities by using known attacks against the selected targets - by OWASP.
*Note that logical vulnerabilities such as broken access control will not be found! And if you want to have better results, manual penetration testing should always be performed in addition.
Active Scan Rules define what kind of vulnerabilities to check for when attacking an application.
To check out the Active Scan Rules feature, go to Tools > Options > Active Scan.
The Active scan will include the following vulnerabilities: .htaccess information leak, Code injection, Command injection, XSS, directory browsing (can lead to directory traversal attack), SQL injection, etc. Also, you can set up a custom policy you want to use when active scanning. Policies will be explained in the next chapter.
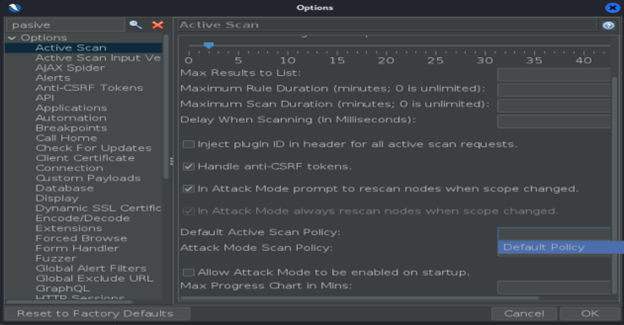
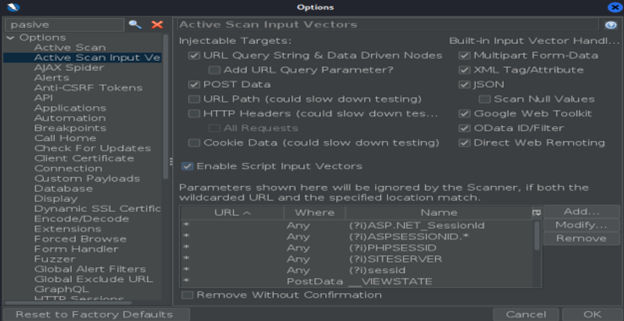
You can read more about passive scan options on this site. To determine what will ZAP attack, you can check out option Active Scan Input Vectors:
Scan Policy Manager
I have mentioned Scan Policy Manager, but what is it?
Scan Policy defines which rules will be run as part of an active scan, how many requests are to be made, and how likely potential issues will be flagged. There is no limit to defining the number of scan policies. Also, as you saw, you can define the default policy to be used for active scans and the attack mode.
To configure policies, go to Analyze tab > Scan Policy Manager, where you can Add, Modify, Remove, and Import/Export policies.

If you want to add a new policy, you can configure it easily. For example, if for your active scan you would like to perform the scan to check out CRLF Injection, you will go to Injection Section and under CRLF Injection, choose Threshold High, and for other injections, choose OFF.

When you finish with the setup, if you would like to perform an active scan with the newly created policy, you can do it like this:

Then click on the Active Scan, choose a policy, and Start Scan!

Conclusion
This is the end of the ZAP short series!
There are plenty of tutorials for using ZAP, and there is the official documentation on the OWASP site you can check out for more better understanding of this tool.